I am working on upgrading our Acumatica instance from 2019R1 to 2021R1. A substantial part of my project involves updating a set of service layer applications that enable bidirectional communication between our ecommerce site and Acumatica. Our web site runs on a platform that does not have an available integration for Acumatica. The site interacts with Authorize.net for all credit card transactions.
I’ll spare everyone the long explanation for why I need to unmask the Payment Profile ID (CCPID) in the API. The TLDR; is “our web site’s integration with Authorize.net could be better”. Most of what I need to accomplish involves not creating duplicate payment methods in Acumatica because of web orders.
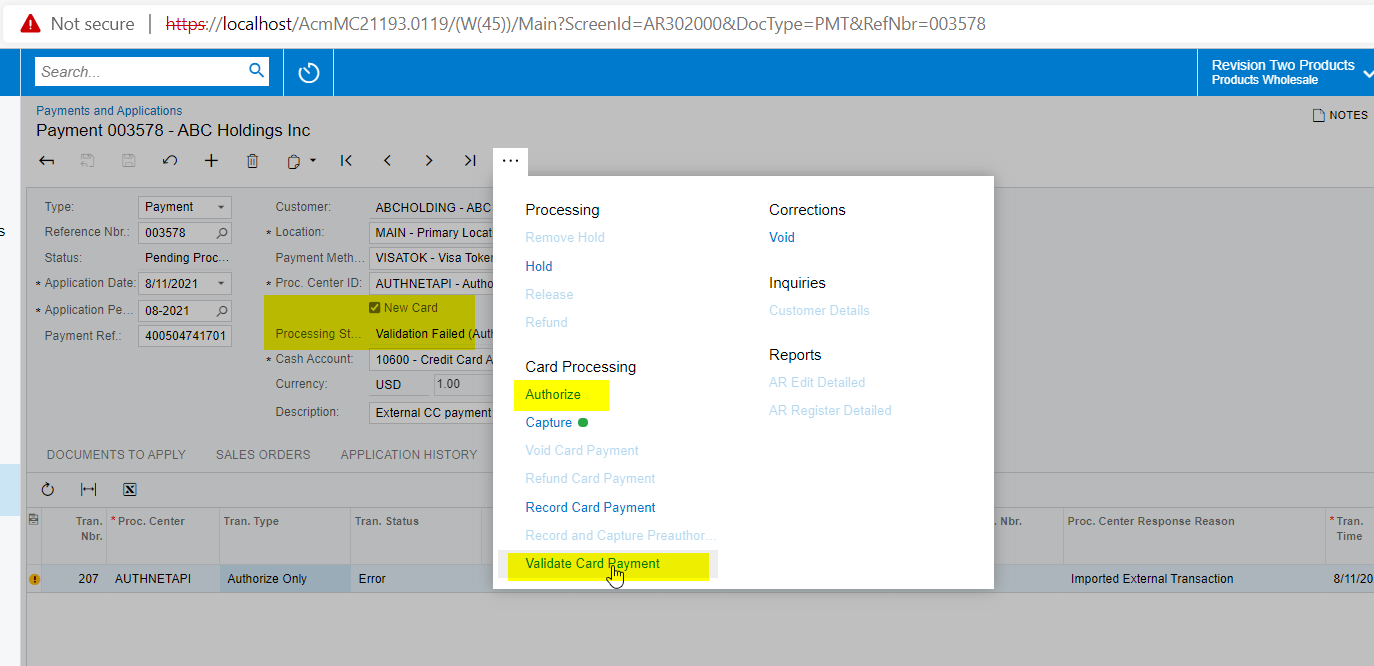
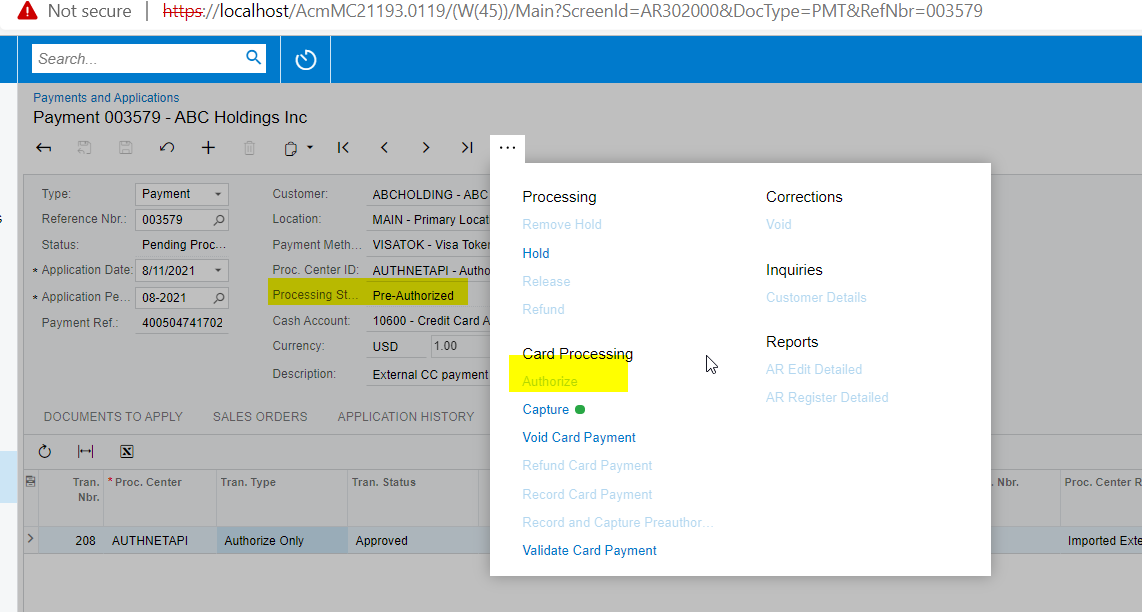
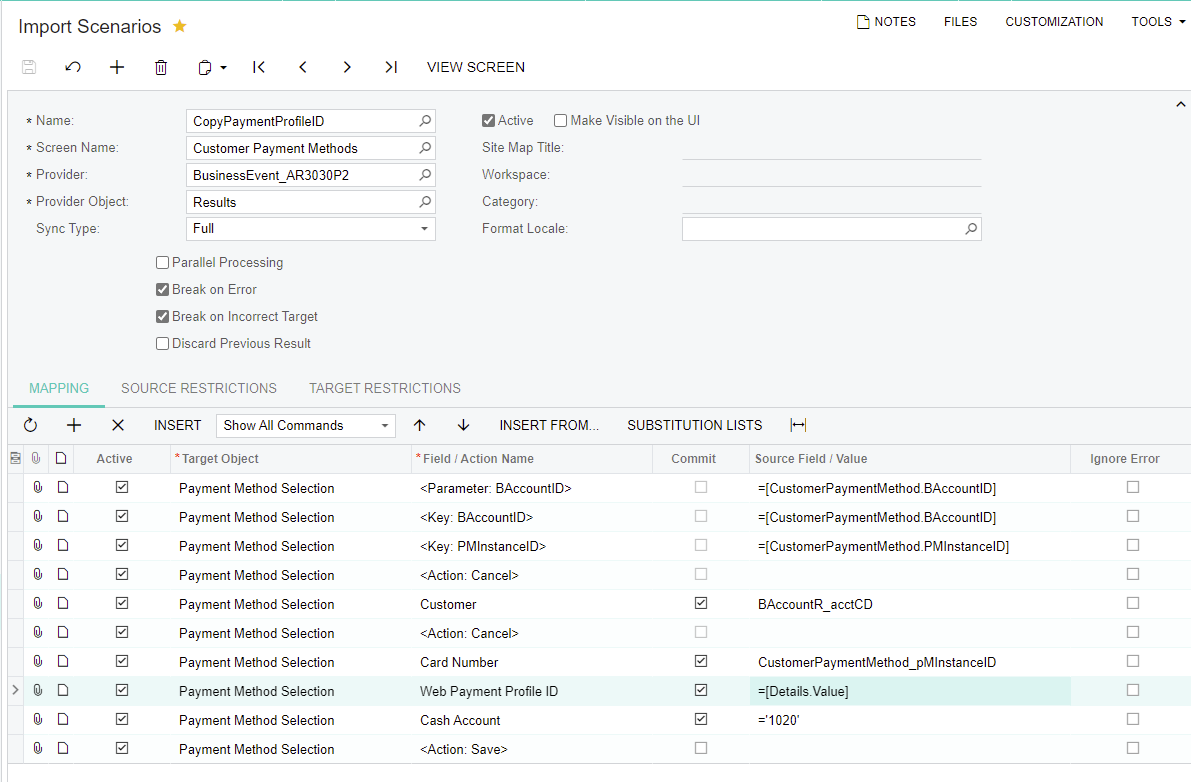
With our customized v18 API endpoint in 2019 R1 my code could load a customer’s payment method list to access the temporary ID for that payment method. A second request was sent to load a single payment method using the temporary ID with the payment method details expanded. That would provide an unmasked CCPID that contained the Authorize.net Payment Profile ID. Based on my testing, this no longer works.
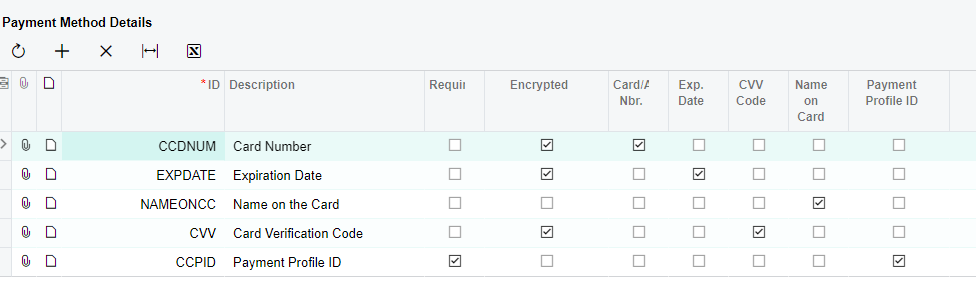
Before I start in on the task of rewriting my code that expects to get a valid Payment Profile ID from Acumatica, I figured I should check if this was something I could change somehow. These payment methods do not have the “Encrypted” checkbox checked for CCPID in the “Settings use in for AR” tab.”
I expect it would be unwise to uncheck the Payment Profile ID checkbox.
As a final thought, I see in the Rest API guide for the recent releases that we can attach externally created credit card transactions in a request to create a sales order (that is great). In that code example there was a line about validation that I’d like to know more about. What does this do when set to true?
"NeedValidation": {"value": true},Thank you!